home
CROP CIRCLE ARTICLES
IMAGERY CROP CIRCLES
Wilton Windmill, May 22 2010.

Wilton Windmill formation. Photo: © Lucy Pringle.
Encryption
This formation seems to depict some kind of program wheel based on binary Ascii codes. I think Karin Alexander of Temporary Temples made it generally accepted the wheel should be interpreted as referring to the famous Euler's identity equation. Yet, there are reasons to argue this, but even if so, the formations essential theme I consider "encryption".
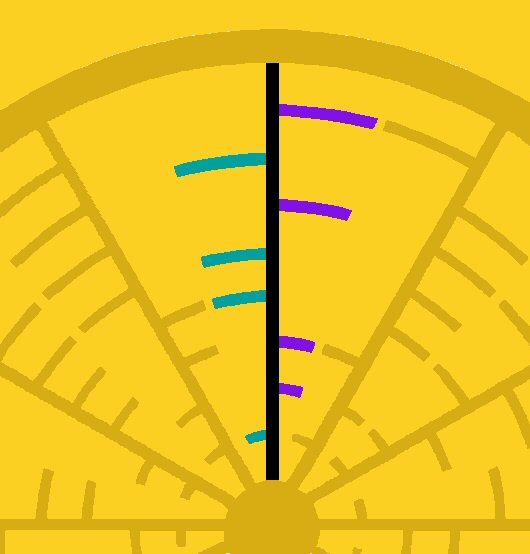
A radial.
Left side branches will accomplish empty spaces on the right side and vice versa.
Noticing the complementary aspect of both sides of the radials in this formation, it gave me a direct sense of finding keys! However, from the expectation there's a message to be decoded (assumption), it can be considered strange and very unlikely that half of the message would be build up by the exact complementary bits of the other half of each radial. It would therefore be reasonable to accept one radial as one key. The only problem we then have is that we need to choose between two options. The left side option or the right side option. Until here it is as if twelve keys are apparent that can be turned in order to fit. So, then I started reasoning that turning these keys would acquire keyholes. From there I began to realise how in fact another twelve radials would fit perfectly between the existing ones! In other words, we can find an invisible wheel containing twelve keys as well!
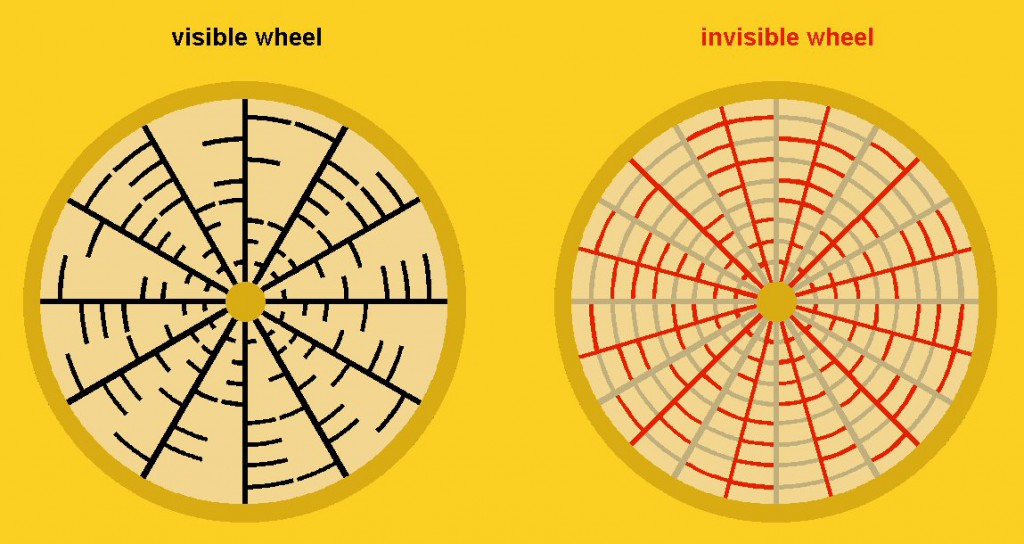
Twelve (red) radials fit perfectly between the existing (black) ones.
To avoid confusion I will remain colouring the visible wheel black and the invisble one red. Interesting about these new found twelve keys is that their left and right halves do not complement each other. For that reason it seems to me as if they are more likely to represent a message than the keys of the visible wheel. On top of this, it also seems that two of these new installed (invisible) radials line out with the windmill directly next to the formation.
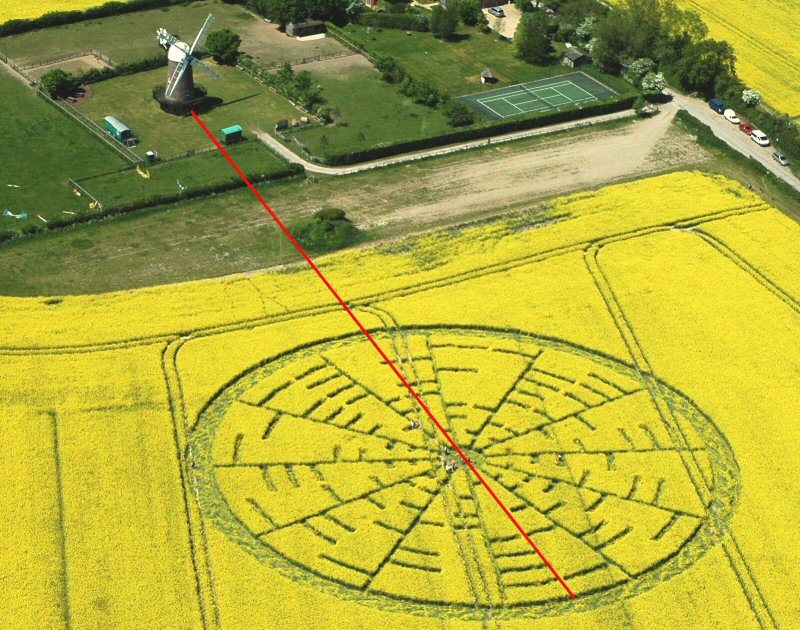
Two of the invisible radials line out with the windmill.
The next step is to create some tables with the binary codes in good order. I won't bore you, dear reader, with these tables. They are just columns of ones and zero's.
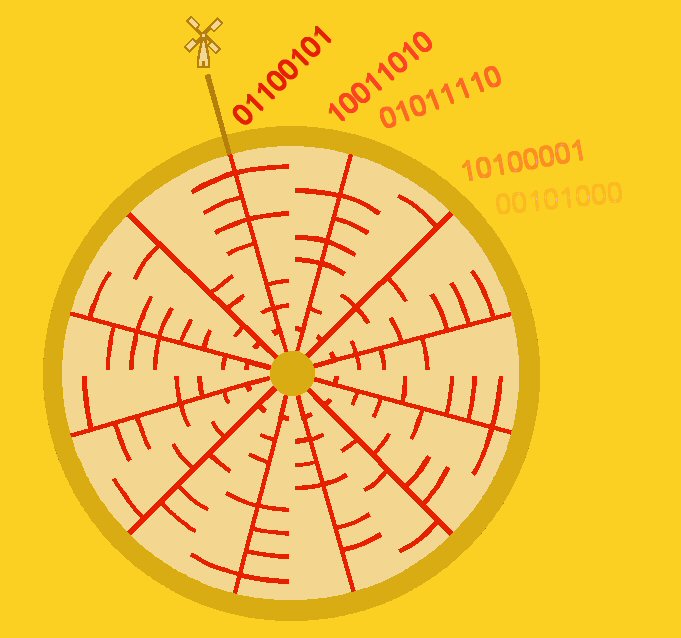
How the codes are found.
A difficulty that appears with mining the binary codes happens with each first of the eight digits. Because each right side of a key starts with a zero and each left side with a one, it seems another deliberate visual order instead of an arrangement relating to a message. Therefore, I can think of this oddity as an indicator that tells us we have to deal with a binary coding system indeed and that we have to start decoding from there. It would mean that we are observing the 7-bits ascii system instead of the common used 8-bits ascii. Another solution, which is actually more of non-solution, is to still use the 8-bits system but ignore the extended codes that start with a one. (These extended codes would lead to a lot of crazy, often unfound symbols anyway.)

Inside the formation, © Andrew Pyrka.
Having concluded the invisible wheel to more likely represents a message than the visible wheel, I continue with the red keys to translate them from 7-bit ascii codes to the symbols or values belonging to these codes.
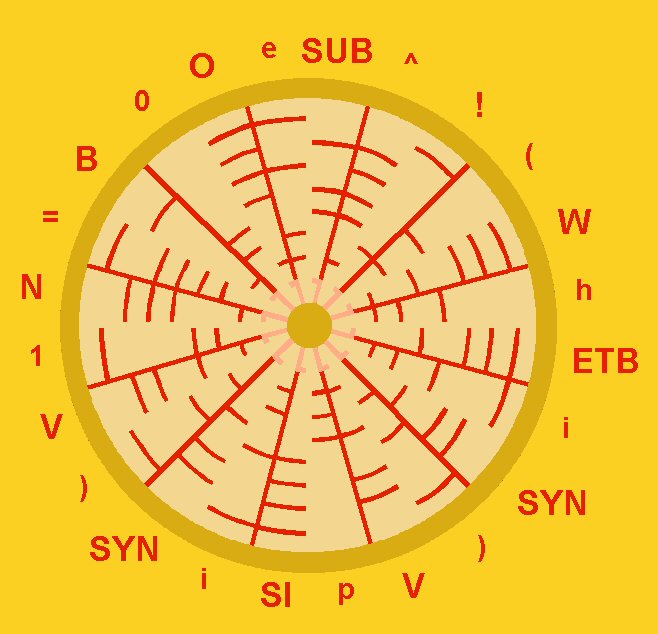
The invisible wheel with values derived from the 7-bit ascii codes.
As the 8-bit ascii system can be considered an extended version of the 7-bit system it should not surprise we find a lot in common between both systems. That's why the left sides of the keys result in a similar fashion as when translated from the 8-bit method. It shows the so called Euler's identity with a remarkable "h" as a mysterious bonus. The right sides show by means of the 7-bit translation a strange combination of capital letters and computing commands, but it is not as exotic and bizar as the right sides would from an 8-bit translation. The equation by decoding the binary language says:
e ^ ( h i ) p i ) 1 = 0
The Euler's identity how it is normally written:
eiπ + 1 = 0
As I understand it, the "h" makes definitly a difference between the two equations. What concerns the rest of the two different notations, I have to leave it to experts to judge if there's a real difference here as I'm not that familiar with mathematical formula's and computer language.
Although the keys of the invisible wheel seem to hold interesting information just by the look of them, we should not forget that they are all combinations of one side together with a complementary side of a neighbouring key. This fact makes it still hard to accept a complete and reasonable decoding will be possible, even when it seems more likely than with the visible wheel. Why then, am I not happy with the equation as the ultimate solution? It is because there's more then double as much information placed in the design as would be necessary!

The equation without extra information.
The diagram above demonstrates a wheel that would already be sufficient to depict the Euler's like equation. It begs the question why we are confronted with all the extra complementary based information? Considering various trajectories (both with 7-bits and 8-bits ascii translations) that resulted in fruitless complications, it becomes acceptable to think that all the extra binary stuff is placed there only to hide the actual information. It looks like a deliberate attempt to diffuse the real message, in this case the so called Euler's identity. Maybe it makes more sense to speak of the identity. Suggesting it isn't necessarily the identity of Euler. Having concluded the extra stuff wants to diffuse the real message, things start to fall in place. We are looking at an encryption devise! It occurs to me this crop circle design is the best visual representation of encrypting that I know of... And concerning the use of an identity as subject for hiding, maybe, the equation should be interpreted as a FALSE identity, as it is not the actual Euler's identity! It would certainly be in tune with the logics of data protection.

Inside the formation, © Andrew Pyrka.
The formation, in my opinion, does not so much idealise the beauty of the Euler equation as much as it expresses the beauty of encryption! I believe the essential meaning of this formation is revealed by this analysis now, but there are two more aspects I would love to shine some light on. First of all, there's the mysterious "h" that is added to the equation. I find, it is screaming for explanation. People like to interpret it as a playful little joke, as if the source is saying "hello" to us. I doubt this to be the real reason, since greeting does not apply to an algebraic formula. An equation can't function with distracting material placed into it. In case we don't want to accept the "h" as a randomly chosen disturber, its presence can only mean that it should be taken as a sincere element in the equation. A little search made it clear to me that this letter most likely stands for "hexadecimal". The imaginary number "i" that follows will therefore have to be a hexadecimal imaginary number! The use of a hexadecimal number system (= 16 base) is common ground in program languages. Introducing the hexadecimal system into the equation feels like a gesture towards the nature of the exposed double 8-bit keys, but I don't have expertise in mathematics, nor in computer science, so I will leave it for what it is. The second aspect I would love to highlight is a very curious one. When observing the visible wheel carefully, one will notice there are 2 sets of keys that are identical.

Two identical sets of keys.
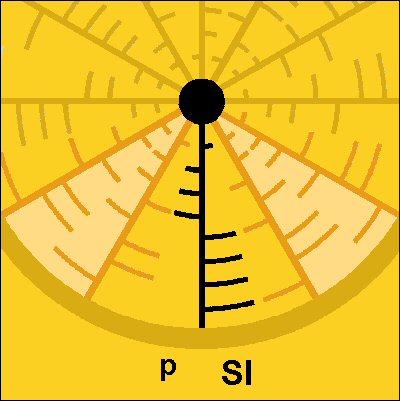
Interpreting the wheel as a key bunch, you almost wonder who could be so stupid to hang his or her spare keys on the same bunch, but this off topic. Anyway, the identical keys are positioned in such a way that it isolates one key in particular. It is this isolated key that attracts all our attention! And therefore I started contemplating over this key, which, by now we know, is an encryption key.
Besides being able to withdraw the binary values "p" and "SI" (SHIFT IN) from the key, it also offers a very original way of looking at it. The picture below will demonstrate how it is possible to find the magic Pi number in it!
Facing the isolated "SHIFT IN p", or simply the "p" key, it made me wonder what particular keyhole it belongs to. Luckily, approximate a week before the report of the Wilton Windmill formation another canola crop formation had appeared at Yarnbury Castle. Two actually in the same field. And guess what? The main one can easily be interpreted as a keyhole!

Yarnbury Castle Formation, 2010 5 16. © Steve Alexander.
About this keyhole formation, I have figured out that it explicitly points to internet spying! An eye peeping through a keyhole leaves us no doubt about the shameful activity. The many dots and parallel lines seem to refer to data points and profiling...
Having found an interesting key that somehow connects with the Yarnbury Castle formation, I like to conclude that we seem advised to use encryption for our internet communication. I wonder how easy accessible that is for the average internet user. It is my firm believe it should be. Shouldn't we be alarmed it isn't?